Hackers haven’t wasted their time in deciding what to do with the proof-of-concept (PoC) called Drupalgeddon 2 code that was published online last week for a major Drupal security flaw.
According to multiple sources, attackers have been steadily infecting servers with backdoor scripts and cryptocurrency-mining malware (coinminers) since last Thursday, April 12.
That was when a Russian security researcher published proof-of-concept code for the Drupalgeddon 2 (CVE-2018-7600) vulnerability affecting all Drupal CMS versions released in the past decade.
Scans for vulnerable sites started within hours after the PoC publication. At the time, speaking to Bleeping Computer, Sucuri CTO and Founder Daniel Cid said most of the attacks they were detecting where tests to see if the PoC was working.
Attacks evolve from PoC testing to dropping actual malware
But things changed over the weekend. Now, multiple sources in the information security industry are reporting that attackers are dropping malicious payloads on vulnerable sites.
For example, Volexity reported on Monday seeing hackers using the public PoC code to drop coinminers, GreyNoise reported seeing a PHP backdoor, while today, the SANS ISC reported seeing attackers drop coinminers, PHP backdoors, and even Perl bots.
The general idea is that attackers tested out the PoC for the first few days, and are now refining payloads before kicking into gear bigger operations. Overall, the number of exploitation attempts is still small, compared to other ongoing malware campaigns, but the numbers are rising.
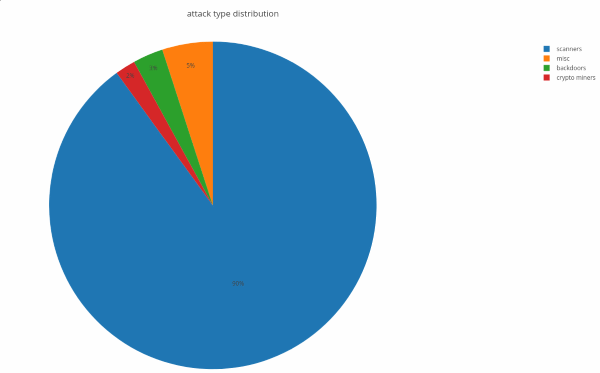
According to statistics collected by Imperva, 90 percent of the attempts to exploit the Drupalgeddon 2 vulnerability are unsuccessful scans, while only three percent are attempts to drop backdoors, and only two percent are attempts to drop a coinminer.
Expert criminal groups are getting involved
Things are surely set to get worse, as Qihoo 360 Netlab experts spotted today three Tsunami botnets that started to actively exploit the Drupalgeddon 2 vulnerability as well.
Similarly, the GreyNoise team has also observed a botnet previously involved in exploiting an Oracle WebLogic flaw, now shifting gears towards the Drupalgeddon 2 vulnerability.
Larger botnets getting involved in the Drupalgeddon 2 scans means that serious threat groups have now turned their sights on this vulnerability and these attackers are more likely to know what they’re doing instead of just testing a PoC.
Exploitation also got a lot easier after the publication of a second PoC on Monday, while some exploit databases added variations on the first PoC —variations that are already weaponized and ready for deployment without additional work from the attacker’s side.
For the time being, even if the Drupal CMS authors have said that “sites not patched by Wednesday, 2018-04-11 may be compromised,” users are still advised to update Drupal sites to versions 7.58 abd 8.5.1, the ones containing fixes for Drupalgeddon 2.