The brute force (or directory bruteforcing) attack is still one of the most popular password-cracking methods. Nevertheless, it is not just for password cracking.
Brute force attacks can also be used to discover hidden pages and content in a web application. This attack is basically “a hit and try” until you succeed. This attack sometimes takes longer, but its success rate is higher.
Basically, any directory brute-forcing attack is based on a couple of parameters:
- Response code,
- Response length.
To start brute-forcing we need to send a request. So in most cases, it will be a simple GET request, but to obtain responses much faster then we’ll need somehow to cut the body, and this way it will be useful to switch for HEAD request. If we don’t need a body it will reduce response size and time, so we can see results faster. Let’s see some interesting and useful tools which can help us to get information about sensitive directories and files on a remote machine.
Dir Buster
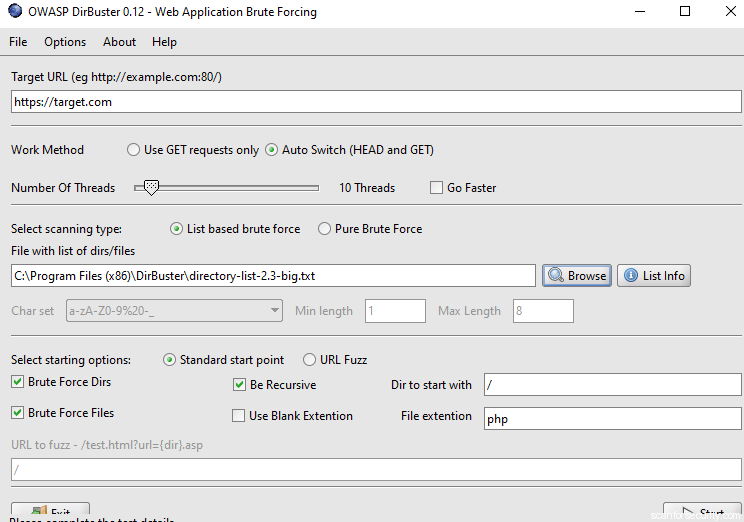
DirBuster is a multi-threaded java application designed to brute force directories and files names on web/application servers. DirBuster comes with a total of 9 different lists; this makes DirBuster extremely effective at finding those hidden files and directories.
How to run:
DirB
DirB is a Web Content Scanner. It looks for existing (and/or hidden) Web Objects. It basically works by launching a dictionary-based attack against a web server and analyzing the response. DirB main purpose is to help in professional web application auditing.
The tool “Dirb” is in-built in Kali Linux, therefore, Open the terminal and type the following command to start a brute force directory attack.
How to run:
$ dirb http://192.168.1.1/dvwa
WFuzz
Wfuzz is a tool designed for brute-forcing Web Applications, it can be used for finding resources not linked (directories, servlets, scripts, etc), brute-force GET and POST parameters for checking different kind of injections (SQL, XSS, LDAP, etc), brute force Forms parameters (User/Password), Fuzzing, etc.
How to use:
$ wfuzz -c -W /usr/share/wfuzz/wordlist/dir/common.txt --hc 400,404,403 http://192.168.1.1/dvwa/FUZZ
Metasploit: HTTP Directory Scanner
This module identifies the existence of interesting directories in a given directory path.
> use auxiliary/scanner/http/dir_scanner
msf auxiliary(dir_scanner) > set dictionary /usr/share/wordlists/dirb/common.txt
msf auxiliary(dir_scanner) > set rhosts 192.168.1.5
msf auxiliary(dir_scanner) > set path /dvwa
msf auxiliary(dir_scanner) >exploit
Dirsearch
Dirsearch is a simple command line tool designed to brute force directories and files in websites. This tool is available at GitHub you can download it from here and after installation in your Kali Linux type following to start dirsearch.
./dirsearch.py –u http://192.18.1.1/ -e php -f -x 400,403,404
Conclusions
Based on this article, we can come to the conclusion that nowadays there are a lot of tools that can help in finding hidden directories and sensitive files.
Despite the fact that the process of searching for such security problems at first glance seems simple, it is not uncommon to find backup files, source files with logins and passwords, git files, and many other interesting things.
A noteworthy point is that most of the tools use the method of sending HEAD requests and with the help of this method the process is accelerated, since part of the body in the answer is completely excluded.






















