Shodan – unique online search engine for vulnerable systems
About Shodan
The unique service called Shodan is a search engine service that lets the users find specific types of computers (routers, web cams, servers and many other services) connected to the internet using a variety of filters.
Some researchers have also described it as a search engine of service banners, which are meta-data the server sends back to the client.
This can be information about the server software, what options the service supports, a welcome message or anything else that the client can find out before interacting with the target server.
How does it works
Search engine “Shodan” collects data mostly on web servers (HTTP & HTTPS ports: 80, 8080, 443, 8443), as well as FTP (port 21), SSH (port 22), Telnet (port 23), SNMP (port 161), SIP (port 5060), and Real Time Streaming Protocol (RTSP, port 554). The latter can be used to access webcams and their video streams.
Service was launched by John Matherly, computer programmer and security researcher in 2009. In 2003 he conceived the idea of searching the devices linked to the internet through some kind of search engine.
The website began as personal project which Matherly based on the fact that large amount of compuer systems and devices are connected to the internet. Later project became public and available for all people.
Users of Shodan search engine are able to find systems including traffic lights, security cameras, home heating systems as well as control systems for water parks, gas stations, water plants, power grids, nuclear power plants most have little to no security.
Many devices use “admin” as their username and “1234” as password, and the only software required to connect to them is a web browser.
The website crawls the Internet for publicly accessible devices, concentrating on SCADA systems. Shodan currently returns 10 results to users without an account and 50 to those with one.
If users want to remove the restriction, they are required to provide a reason and pay a fee. The primary users of Shodan are cybersecurity professionals, researchers and law enforcement agencies. While cybercriminals can also use the website, some typically have access to botnets that could accomplish the same task without detection.
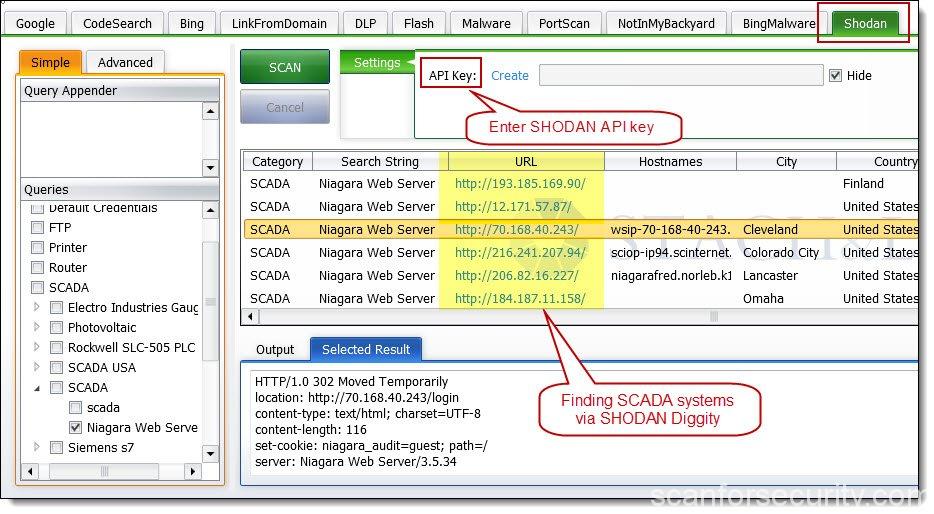
Shodan Diggity & API
Bulk searching and processing of SHODAN queries can be performed using SHODAN Diggity (part of SearchDiggity, Bishop Fox’s free search engine attack tool suite).
The free tool provides an easy-to-use scanning interface to the popular hacking search engine via the SHODAN API.
SHODAN Diggity comes equipped with convenient list of 167 search queries ready in a pre-made dictionary file, known as the SHODAN Hacking Database (SHDB).
This dictionary helps target various technologies including webcams, printers, VoIP devices, routers, toasters, switches, and even SCADA/Industrial Control Systems (ICS) to name just a few.
Basic usage
You start by navigating to the main page, and then entering into the search field, like you would any other search engine. You can search for “ftp” or “vnc” for example, just type name of the service into the search field and that’s it.
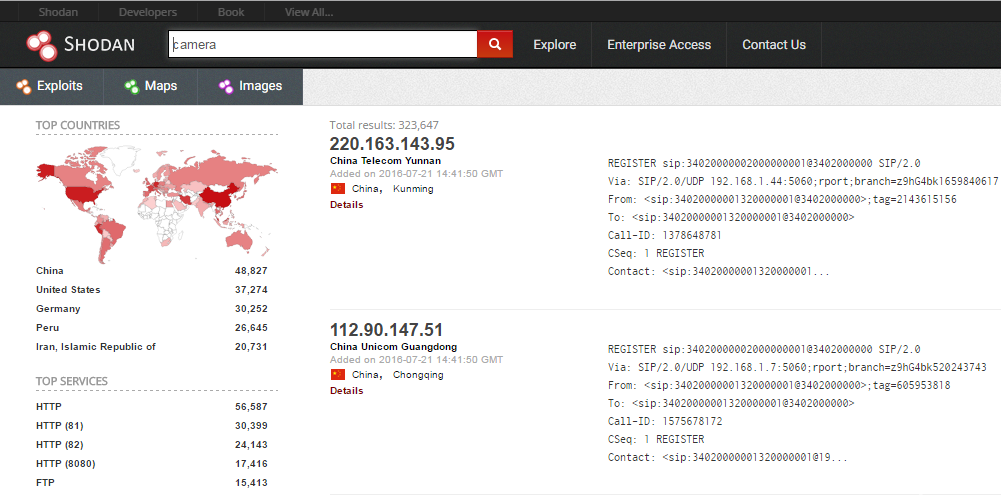
From there you can pivot to a few key areas in the results. Starting on the left sidebar, we see a good amount of summary data:
- Results map
- Services (Ports)
- Organizations (ISPs)
- Operating systems
- Products (Software name)
Then in the main section we get the full results list, including:
- IP address
- Hostname
- ISP
- When the entry was added to the database
- The country it is located in
- The banner itself
How to use filters
Here are the basic search filters you can use:
city: find devices in a particular citycountry: find devices in a particular countrygeo: you can pass it coordinateshostname: find values that match the hostnamenet: search based on an IP or /x CIDRos: search based on operating systemport: find particular ports that are openbefore/after: find results within a timeframe
Usage examples of Shodan filters
Find Apache servers in New York:
apache city:"New York"
Find GWS (Google Web Server) servers:
"Server: gws" hostname:"google"
Find Cisco devices on a particular subnet:
cisco net:"192.168.13.0/24"
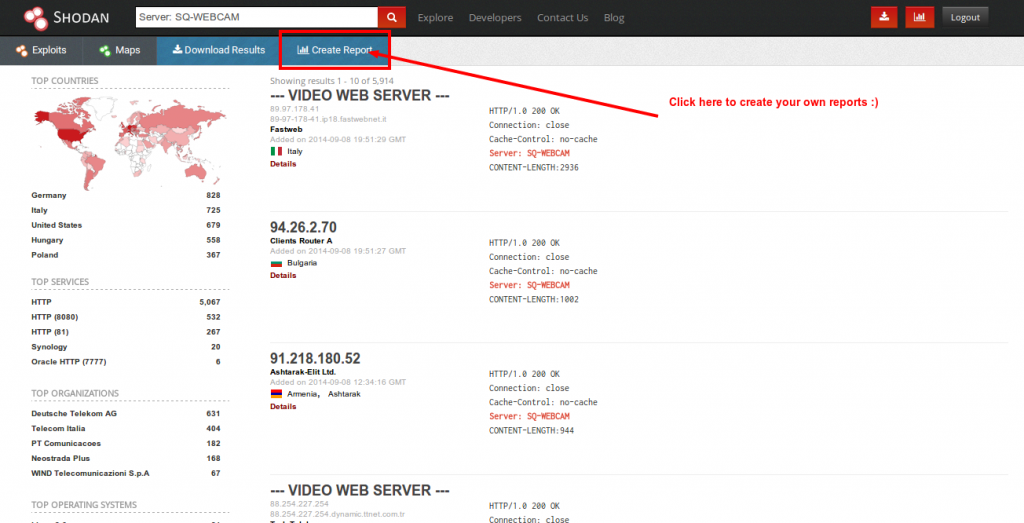
Reporting
Data Export feature allows you to export your results in various formats using the top menu after you’ve performed a search.
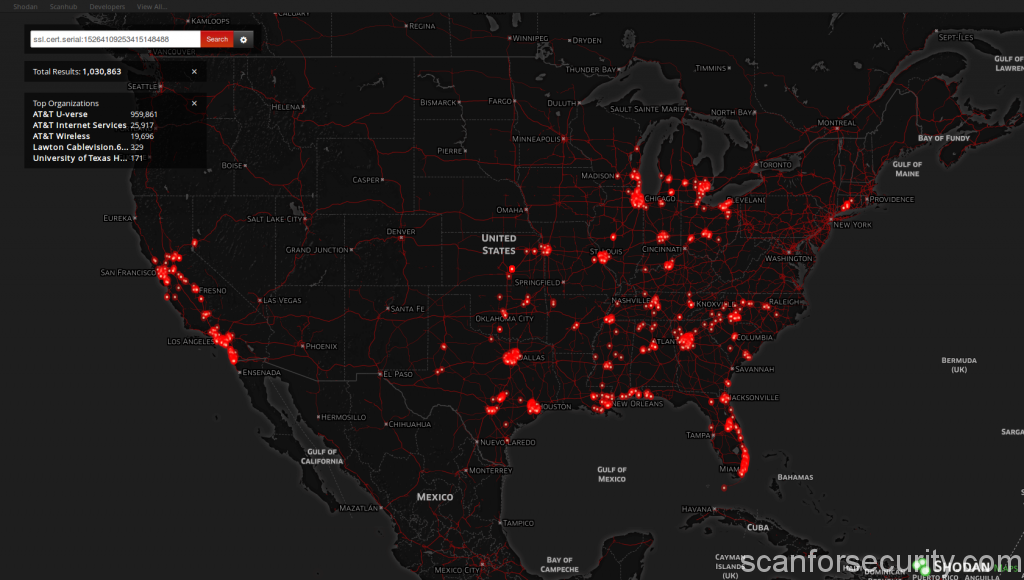
Shodan Maps
Provides a new and easy way to search for devices on the Internet and see the results on a map instead of a regular search listing. When you zoom into an area, it will narrow down your search results to only show devices that are within the viewable area.
Essentially it works and behaves the same way as every other map search service like Google Maps, Bing Maps etc. It will currently display up to 1,000 results at a time on-screen as well as summary information about all the results such as top 5 services, organizations and countries.
Note that it may take up to 40 plus seconds sometimes to complete a search, depending on how far zoomed out you are and how many results there are in total.
How Matherly monetized his search service
John Matherly pays for all of this by charging security companies big money for access to his entire database. Anybody can query Shodan, but if you want to do more than a handful of searches you have to register, and then eventually pay a one-time fee to use the site.