What is network security
First of all, let’s try to understand what is network security and on the next step we going to list and discuss security tools for effective network security scanning. As without understanding for what do we need this – it doesn’t matter what kind of tool to use, so let’s begin and do things properly.
Network security consists of the policies and practices adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources.
- Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority.
- Network security covers a variety of computer networks, both public and private, that are used in everyday jobs; conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access.
- Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done.
All an attacker needs is just to find one vulnerability to get chance and break into a foothold in your network. That’s why there are some minimum security requirements available. You should scan your network at least once a month and patch or remediate identified vulnerabilities.
Although some compliance requirements require you to scan your network quarterly and at least yearly execute penetration testing. These critical assets need special attention, so develop a risk tolerance level for the minimum days your organization can go before those assets are scanned and patched. You can automate your scan tool to scan certain devices and web apps at specific times, but scan only after you remediate all vulnerabilities to show progress in your security efforts.
There are two popular approaches available for vulnerability scanning, authenticated and unauthenticated scans:
- Unauthenticated method, the tester performs the scan as an intruder would, without trusted access to the network. Such a scan reveals vulnerabilities that can be accessed without logging into the network.
- Authenticated scan, the tester logs in as a network user, revealing the vulnerabilities that are accessible to a trusted user, or an intruder that has gained access as a trusted user.
As a matter of fact, the best network scanners are those that provide flexibility for your changing requirements and network security requirements. We going to list not only open source and free solutions, but also commercial solutions which can be used for free in some cases of course with limitations applied.
Network Security Scanners
nmap
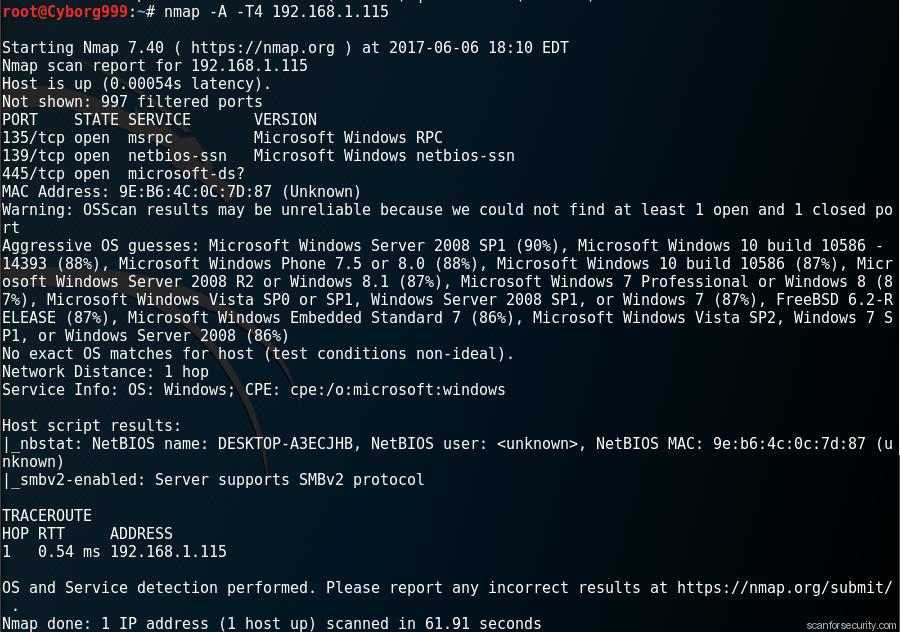
Here the first and most popular solution – usage of free and open nmap network vulnerability and open ports scanner. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X.
hping3
hping3 is a command-line oriented TCP/IP packet assembler/analyzer. The interface is inspired to the ping(8) unix command, but hping isn’t only able to send ICMP echo requests. It supports TCP, UDP, ICMP and RAW-IP protocols, has a traceroute mode, the ability to send files between a covered channel, and many other features.
Default protocol is TCP, by default hping3 will send tcp headers to target host’s port 0 with a winsize of 64 without any tcp flag on. Often this is the best way to do an ‘hide ping’, useful when target is behind a firewall that drop ICMP. Moreover a tcp null-flag to port 0 has a good probability of not being logged.
hping3 can be used for:
- Firewall testing
- Advanced port scanning
- Network testing, using different protocols, TOS, fragmentation
- Manual path MTU discovery
- Advanced traceroute, under all the supported protocols
- Remote OS fingerprinting
- Remote uptime guessing
- TCP/IP stacks auditing
- hping can also be useful to students that are learning TCP/IP
In addition to the discovery capabilities that have already been mentioned, hping3 can also be used to perform a TCP port scan. To perform a port scan with hping3, we need to use the --scan mode with an integer value to indicate the port number to be scanned.
Arp-scan
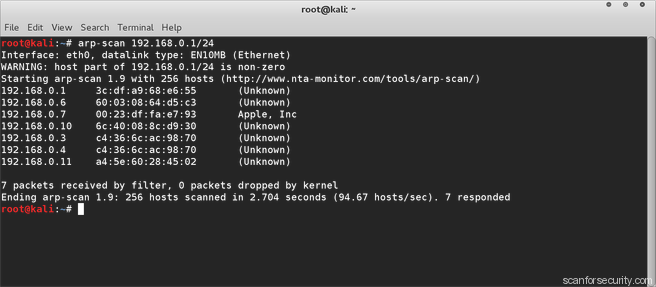
The ARP Scan Tool (AKA ARP Sweep or MAC Scanner) is a very fast ARP packet scanner that shows every active IPv4 device on your subnet. Since ARP is non-routable, this type of scanner only works on the local LAN (local subnet or network segment).
The ARP Scan Tool shows all active devices even if they have firewalls. Devices cannot hide from ARP packets like they can hide from Ping. To find active IP addresses outside your subnet, use the Ping Scan Tool (a Ping Sweep tool – NetScanner).
arp-scan sends ARP packets to hosts on the local network and displays any responses that are received. The network interface to use can be specified with the –interface option. If this option is not present,arp-scan will search the system interface list for the lowest numbered, configured up interface (excluding loopback). By default, the ARP packets are sent to the Ethernet broadcast address, ff:ff:ff:ff:ff:ff, but that can be changed with the –destaddr option.
OpenVAS
OpenVAS is a full-featured vulnerability scanner. Its capabilities include unauthenticated testing, authenticated testing, various high level and low level Internet and industrial protocols, performance tuning for large-scale scans and a powerful internal programming language to implement any type of vulnerability test.
Greenbone develops OpenVAS as part of their commercial vulnerability management product family “Greenbone Security Manager” (GSM). OpenVAS is one element in a larger architecture. In combination with additional Open Source modules, it forms the Greenbone Vulnerability Management solution. Based on this, the GSM appliances use a more extensive feed covering enterprise needs, a GVM with additional features, appliance management and a service level agreement.
In 2019 the branding separation was completed. OpenVAS now represents the actual vulnerability scanner as it did originally. The framework where OpenVAS is embedded is the Greenbone Vulnerability Management.
Nessus
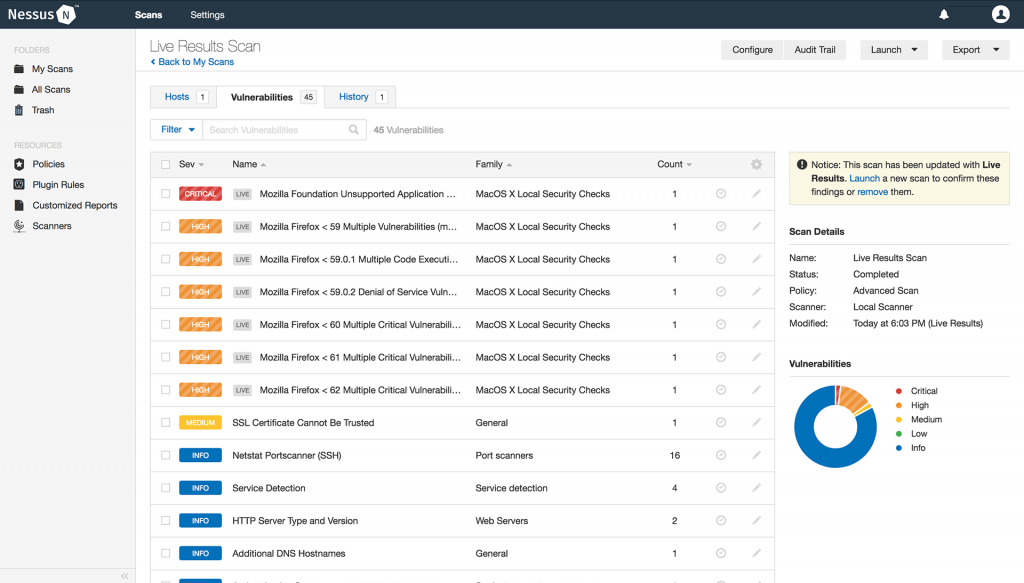
Nessus was built from the ground-up with a deep understanding of how security practitioners work. Every feature in Nessus is designed to make vulnerability assessment simple, easy and intuitive. The result: less time and effort to assess, prioritize, and remediate issues.
Initially, Nessus consisted of two main components; nessusd, the Nessus daemon, which does the scanning, and nessus, the client, which controls scans and presents the vulnerability results to the user. Later versions of Nessus (4 and greater) utilize a web server which provides the same functionality as the client.
In typical operation, Nessus begins by doing a port scan with one of its four internal portscanners (or it can optionally use AmapM or Nmap) to determine which ports are open on the target and then tries various exploits on the open ports. The vulnerability tests, available as subscriptions, are written in NASL (Nessus Attack Scripting Language), a scripting language optimized for custom network interaction.
Nessus allows scans for the following types of vulnerabilities:
- Vulnerabilities that allow a remote hacker to control or access sensitive data on a system.
- Misconfiguration (e.g. open mail relay, missing patches, etc.).
- Default passwords, a few common passwords, and blank/absent passwords on some system accounts. Nessus can also call Hydra (an external tool) to launch a dictionary attack.
- Denials of service against the TCP/IP stack by using malformed packets
- Preparation for PCI DSS audits
The Nessus vulnerability database is updated daily. However, because of the modularity of Nessus it is also possible for you to create your own unique plugins to test against. Nessus is also smart enough to test services running on non-standard ports, or to test multiple instances of a service (for instance if you are running an HTTP server on both port 80 and port 8080).
For free usage you can get official nessus home licence and use it for internal scans without limitations, for external scans it is limited with only 16 targets.
Masscan
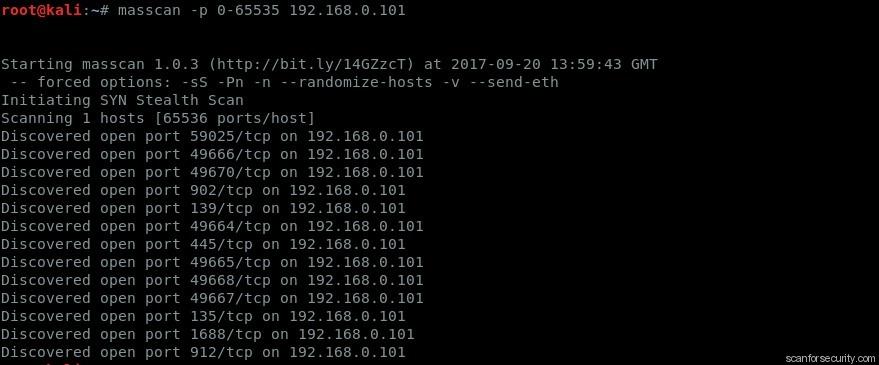
This is the fastest Internet port scanner. It can scan the entire Internet in under 6 minutes, transmitting 10 million packets per second.
It produces results similar to nmap, the most famous port scanner. Internally, it operates more like scanrand, unicornscan, and ZMap, using asynchronous transmission. The major difference is that it’s faster than these other scanners. In addition, it’s more flexible, allowing arbitrary address ranges and port ranges.
NOTE: masscan uses a custom TCP/IP stack. Anything other than simple port scans will cause conflict with the local TCP/IP stack. This means you need to either use the -S option to use a separate IP address, or configure your operating system to firewall the ports that masscan uses.
Masscan can detect whether ports are open, but it can also complete the TCP connection and interaction with the application at that port, and grab the simple “banner” information.
This tool is suitable in case if you have huge internal and/or external networks to scan for possible open ports and banners information grabbing to compare results with available vulnerabilities databases like exploit-db or vulners and determine possible holes in security.
You can get masscan from official github repository and also find there installation guide. Don’t forget to set up port on firewall for proper banners grabbing.
Conclusion
From this article you can see, that there are various tools available for effective network security scanning and vulnerabilities identification. From my experience even with set of open source tools you can try and build your own custom solution which will be useful for internal audits and scans.
Most of solutions are expensive and have high system requirements if speak for example about Nexpose from Rapid7, but in this case we can find fine alternative in the face of free OpenVAS or commercial solution like Nessus or even make something with OpenVAS and ZAProxy.
























