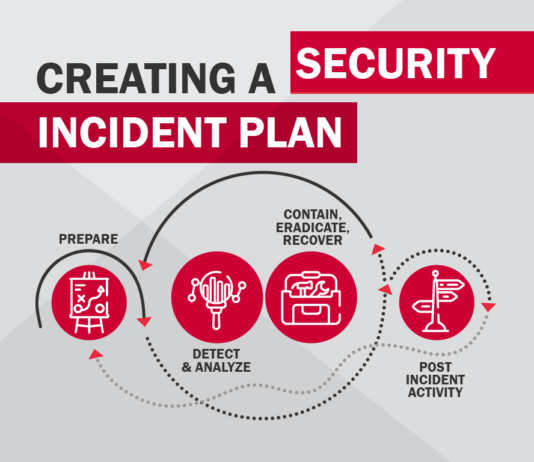
How to protect web app on PHP from simple DDoS attacks
Quite recently an advertising article about the anti-DDoS attacks at the application level appeared on the hub. I had a similar experience of searching for the optimal algorithm for countering attacks,...
How to hijack RDS session
RDP hijacking — how to hijack RDS and RemoteApp sessions transparently to move through an organisation. How you can very easily use Remote Desktop Services to gain lateral movement through a...
About Bug Bounty Programs and Most Popular of Them
Very popular among hackers to surf internet in the search of bugs and wide variety of websites: manually, with scanners, using search engines etc
Why hackers do this? Many years go was...
API Exploits or How To Make API More Secure
As abundant of the software and application development companies are shifting to the APIs, the danger of security breaches has enhanced to a great extent. This is because of the circumstance...
6 steps for organizations to better protect customer data
Today very hard to protect customer data and your personal information from hacks and leakages, if somebody interested in your data - than be ready soon it can be published in...