BlackWidow is a python based web application spider to gather subdomains, URL’s, dynamic parameters, email addresses and phone numbers from a target website. This project also includes Inject-X fuzzer to scan dynamic URL’s for common OWASP vulnerabilities.
Available commands and options
Usage: blackwidow [options]
Options:
-h, --help show this help message and exit
-u URL, --url=URL Full URL to spider
-d DOMAIN, --domain=DOMAIN
Domain name to spider
-c COOKIE, --cookie=COOKIE
Cookies to send
-l LEVEL, --level=LEVEL
Level of depth to traverse
-s SCAN, --scan=SCAN Scan all dynamic URL's found
-p PORT, --port=PORT Port for the URL
-v VERBOSE, --verbose=VERBOSE
Set verbose mode ON
BlackWidow tool can be used on first steps of application/server vulnerability assessment for information gathering process. As it includes “Inject-X” fuzzer – it also can be used for detection of such vulnerabilities like Cross-Site Scripting (XSS) or SQL Injection (SQLi) as well as identify possibilities for HTML code injection.
Let’s try to run it against our website:
$ blackwidow -d scanforsecurity.com
Here we can see the results:
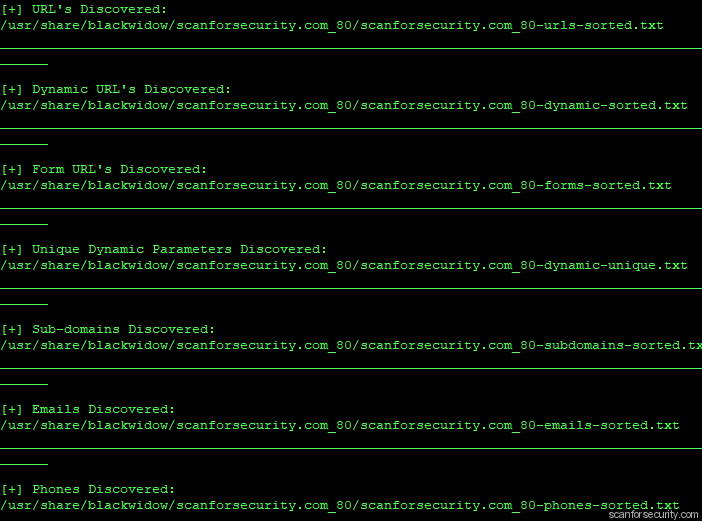
If check our loot, actually we’ll find nothing as this website runs via https protocol and by default it was checked through http only. So our option will be to use blackwidow with “-u” key.
$ blackwidow -u https://www.scanforsecurity.com
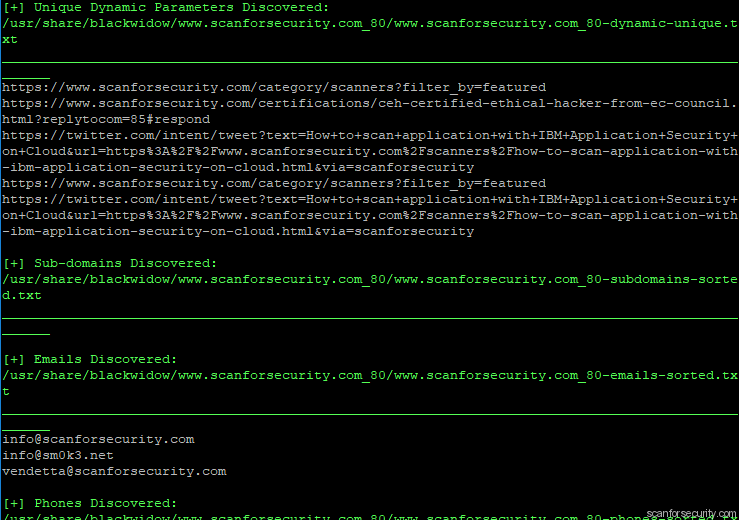
As you can see, now in the results we can find emails, dynamic urls and some other information which later can be used with fuzzers and bruteforcers.
Together with this tool you can also use such tools like sqlmap and XSSer for example. Emails can be bruteforced with some other kind of tools.
Official tool repository at GitHub

























web application scanner osint fuzzer owasp vulnerability python spider passive active sqli xss lfi rfi rce csrf automated scan bugbounty
i have error in the tool while running in my kali linux …after searching blackwidow -u and https://target.com it gives result and shows no such directory and give the path of directory….what is problem?
If you talk about storing of the results – possibly user under which you run this tool has not enough prvivileges to create folders/files.
Another thing – possibly target website is unavailable or accessible only via HTTP. Need a bit more information on your case.
Comments are closed.